In an ever-evolving landscape where security and compliance are paramount, innovation becomes the driving force that can redefine the status quo. Today, we are thrilled to introduce a transformative leap that promises to revolutionize the entire Cyber GRC world. Prepare to embark on a journey that unveils the game-changing marvel of Cypago’s No-Code Automation Workflows.
In this blog, we will not only introduce you to the revolutionary concept of No-Code Automation Workflows but also delve deep into the profound benefits they bring to the forefront for CISOs and GRC managers across organizations of all sizes. Get ready to witness a groundbreaking paradigm shift in how security and compliance challenges are met and conquered.
What are No-Code Automation Workflows?
No-Code Automation Workflows serve as your paramount tool for automating your entire security program and orchestrating the meticulous GRC processes of security control testing, validation, continuous control monitoring and evidence collection. Through these workflows, you wield the reins to finely-tune every aspect of evidence collection and gap analysis. This powerful feature empowers you with the ability to build from scratch, or edit and customize, how evidence is gathered and scrutinized, ensuring that the process aligns precisely with your organization’s control testing , validation needs, and your security and compliance programs.
No longer confined to rigid methodologies, you can tailor evidence collection and control testing to fit your specific security and compliance landscape, enabling a more nuanced and effective approach to managing your organization’s risk and regulatory requirements. It’s here that you can incorporate the rigorous assessments required for security and compliance gap analysis, identifying deviations from standards and pinpointing areas requiring immediate attention.
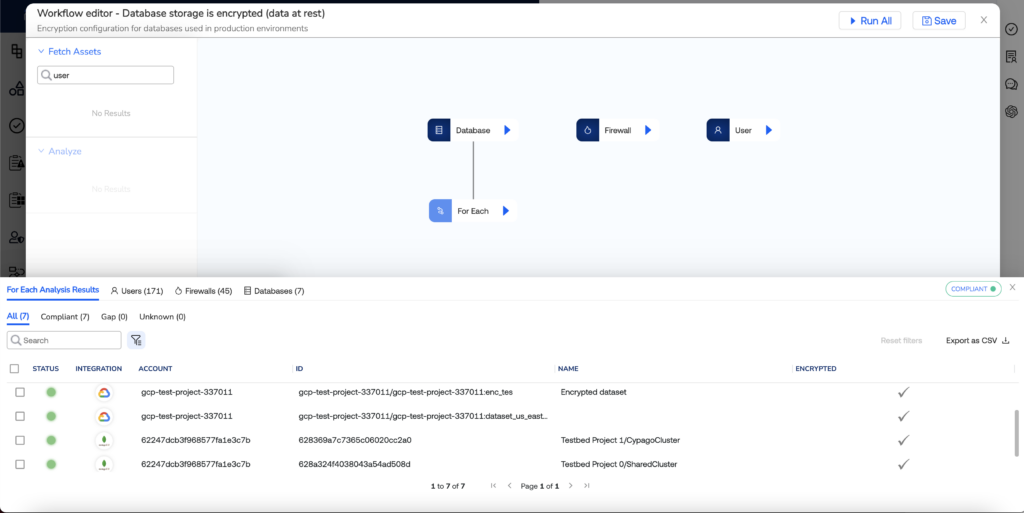
In essence, with the flexibility and adaptability of workflows, you’re not just collecting data but orchestrating a comprehensive and responsive system for control testing, validation, security and compliance gap analysis, and continuous control monitoring. This level of control and customization empowers you to navigate the complex landscape of modern IT environments with precision and confidence.
Precision Engineering for Security Excellence
No-Code Automation Workflows transcend the conventional notion of features; they represent a monumental innovation that redefines the cybersecurity and compliance landscape. These workflows empower users to become the architects of their security strategies and programs, allowing them to engineer, build, program, orchestrate, and automate intricate processes with a remarkably accessible, flexible, easy to use, no-code interface.
This groundbreaking capability serves as the linchpin of the platform, forming the very foundation upon which all automation and operations are built. It is not merely a feature but the cornerstone of Cypago’s pioneering approach to cybersecurity and compliance.
With no-code automation workflows, users have the power to construct, program, define, and execute complex processes seamlessly across multiple environments. This capability is a testament to Cypago’s commitment to offering a transformative and industry-redefining solution for security and compliance.
The precision orchestration facilitated by these workflows optimizes the deployment of security controls and compliance measures, ushering in an era where every facet of an organization’s security landscape is meticulously tailored for excellence. In essence, no-code automation workflows are the driving force behind Cypago’s ability to provide unparalleled levels of control, automation, and precision in today’s dynamic and ever-evolving cybersecurity and compliance landscape.
We Let You Build Your Security Program and Controls
No code automation workflows are seamlessly integrated into the Cypago Cyber GRC Automation (CGA) platform architecture, offering a dynamic canvas for the creation of security programs and controls that are uniquely tailored to each organization. The result? Bespoke Cyber GRC processes, plans, and policies that are molded to the precise contours of an organization’s infrastructure and operational landscape. Once meticulously crafted strategies are established, they are effortlessly propagated across diverse systems – whether they reside in on-premises infrastructure or expansive cloud environments. This automation not only enhances operational efficiency but also ensures compliance adherence with unwavering precision – giving you end-to-end control over your Cyber GRC Automation processes in a single pane of glass.
Where Vision Meets Implementation: CISOs and GRC Teams Take the Lead
This exceptional capability isn’t just a tool; it’s a paradigm shift. For Chief Information Security Officers (CISOs) and Governance, Risk, and Compliance (GRC) teams, workflows position them at the forefront of innovation in security implementation. Through workflows, these professionals can recalibrate policies, plans, and procedures — architecting blueprints that mirror their organization’s unique operational fabric.
A Symphony of Security: Unifying Vision, Implementation, and Automation
Cypago’s no-code automation workflows introduce an advanced level of automation to Cyber GRC programs and controls, elevating governance precision by orchestrating the meticulous retrieval and analysis of information. This platform empowers organizations with a panoramic view of their security and compliance landscape, spanning hybrid multi-cloud IT environments and tools. Cypago’s capabilities open the door to tangible use cases, transforming theoretical concepts into practical use cases that illuminate the benefits and values of our platform. Let’s explore how these capabilities relate to a real-world scenario.
Use Case: NIST CSF/NIST 800-53
In a scenario involving organizational adherence to NIST Cybersecurity Framework (CSF) or NIST 800-53 security and privacy control catalog using Cypago, the process seamlessly unfolds. Initially, specific controls, such as “Encryption Status” within NIST standards, are defined with hundreds of out-of-the-box default control automations workflows that can be always further customized..
Data encryption controls are just one example. Data encryption controls serve as just one illustration. Cypago, in turn, enables the organization to formulate the necessary procedures for autonomously gathering encryption configuration data, encompassing queries across various systems and endpoints to amass encryption details. After configuration, Cypago takes the reins of data collection, ensuring precision almost in real-time. It stands ready to detect and record any alterations in network encryption status, including the encryption of all data sources within the organization, such as databases, data lakes, data warehouses, servers, and endpoints, among others.
The subsequent step involves defining control testing, validation, and gap analysis logic. Organizations establish criteria and rules for assessing collected data against NIST Cybersecurity Framework or NIST 800-53 controls, e.g., validating encryption status across applicable systems and identifying deviations.
Cypago offers a user-friendly interface for configuring these logic rules, catering to both cybersecurity experts and non-technical personnel. Automation then takes center stage, applying established rules to incoming data, mitigating human error, and ensuring consistent assessments. Detected anomalies or non-compliance issues prompt instant alerts, enabling swift corrective actions.
Cypago further integrates with remediation workflows, automatically triggering responses to non-compliance or security gaps, like notifying IT teams, implementing patches, or restricting access. This automation minimizes vulnerability windows and security risks.
Continuous monitoring and optimization follow suit, with Cypago capturing historical data, tracking trends, and providing insights for refining control logic and remediation strategies. Its adaptability keeps organizations proactive in maintaining compliance.
In summary, Cypago aids data collection, control logic definition, and automation, supporting organizations throughout the control adherence lifecycle. It ensures preparedness and continuous monitoring for rigorous standards like the NIST Cybersecurity Framework or NIST 800-53 control standards.
Cypago’s Precision and Customization Capabilities in Action
As we delve deeper into the capabilities of Cypago, it becomes evident that precision and customization are at the core of its functionality. It empowers organizations to define data sources, filter evidence, create bespoke control analysis logic, and employ complex rules, all for the singular purpose of mastering the intricacies of modern IT landscapes.
Imagine a Chief Information Security Officer (CISO) seeking to fortify their organization’s cybersecurity program by implementing internal security policies tailored precisely to their needs. Now, let’s explore how these capabilities work together to enhance the CISO’s cybersecurity and compliance efforts.
Defining Your Data Sources for Greater Precision
At the heart of Cypago’s No-Code Automation Workflows lies the ability to define and aggregate data sources. But why is this crucial? By defining your sources, you pinpoint the origins of your data, enabling a granular understanding of where potential vulnerabilities or compliance gaps might exist. Without this capability, you’d be navigating in the dark, unable to trace back issues to their roots.
Filtering Evidence for More Meaningful Insights
Filtering evidence and data is about sifting through the noise to extract meaningful insights. Imagine drowning in a sea of information, much of it irrelevant to your security or compliance concerns. Filtering allows you to focus on what truly matters, saving time, resources, and enhancing your ability to detect and respond to critical threats or compliance breaches.
Building Control Analysis Logic/Algorithms for Bespoke GRC
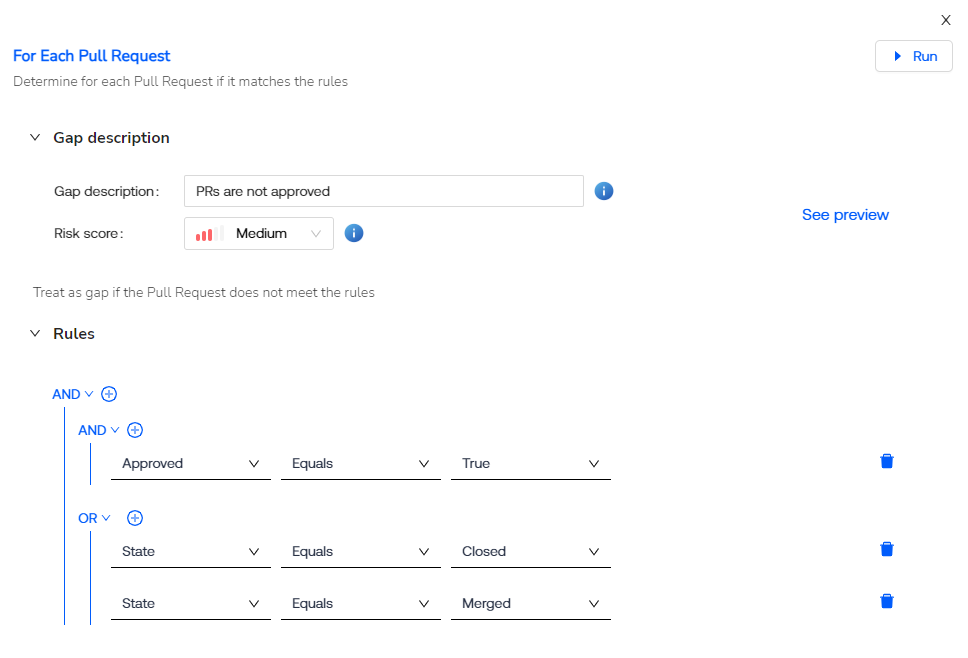
The ability to build control analysis logic and algorithms is like crafting a finely-tuned instrument. Why is this important? It empowers you to create customized, context-aware rules that align with your specific security and compliance needs. One-size-fits-all solutions often fall short, but with tailored logic, you gain precision in identifying risks and ensuring adherence to regulations.
Harness The Full Power of Logic with No Code Automation Workflows
The Cyber GRC landscape is seldom straightforward; it’s a web of interconnected requirements, systems and data. To really achieve immense automation that gets you covered, rigidness is your foe while flexibility, freedom and tailored logic is your comrade.
Cypago provides you that freedom with the unlimited power of defining and building your own logic to implement your security controls.
Using a no-code interface, you can define advanced and nested rules and conditions, evaluate expressions, compare different sets of data, define verdicts and actions, and ultimately program your security and compliance program to produce automation that really works.
Those advanced but yet easy to configure elements, together, allow you to address multifaceted scenarios that may require multiple conditions or components assembled together to tell and automate the whole security control story.
In essence, Cypago’s no-code automation workflows empower your team with limitless automation and continuous monitoring – for one crucial reason: to provide you with the tools necessary to build and monitor your security and compliance programs. By doing so, it ensures that you can effectively safeguard your organization’s security and maintain compliance with confidence and precision.
For a personalized demonstration of how Cypago’s no-code automation workflows can be implemented in your organization, schedule a demo with us now.
