In the ever-evolving landscape of cybersecurity, Chief Information Security Officers (CISOs) grapple with multifaceted challenges, navigating the intricate web of User Access Reviews (UARs) and the ominous specter of tool sprawl. As organizations strive to fortify their digital perimeters, the concept of orphan users has emerged as a pivotal concern within the realm of user access management. Orphan and dormant users have the potential to serve as entry points for both inside and outside threats. Abandoned or inadequately managed accounts pose security risks, enabling unauthorized access and exploitation by malicious insiders. Effectively addressing orphan users is crucial to mitigate the risk of data breaches, insider attacks, and compliance violations, ensuring a robust defense against evolving cybersecurity threats. In this dynamic environment, Cypago stands as a formidable ally, wielding a powerful arsenal to address the security gaps associated with orphan users and alleviate the tool sprawl predicament faced by CISOs. Let’s delve into the intersection of UARs, orphan users, and the innovative solutions that Cypago brings to the forefront.
Understanding the Orphan User Dilemma
Orphan users, within the realm of User Access Reviews (UARs), refer to users who lack a corresponding employee profile within the organization or any other legitimate software service. In simpler terms, these are users who are no longer actively employed by the company. If not effectively identified and managed, these orphan users present a formidable threat to the organization’s security infrastructure. Handling the identification and management of orphan users manually introduces several intricacies and challenges for organizations. Here are some key aspects to consider:
- Scale and Volume: In large enterprises with numerous applications and a substantial user base, the sheer volume of data makes manual tracking and identification of user accounts a daunting task. The potential for oversight increases exponentially as the number of users and applications grows.
- Employee Turnover: Managing orphan users becomes especially challenging in dynamic environments where employees join, leave, or change roles frequently. Manually updating user lists to reflect changes in employee status requires meticulous attention and is prone to human error.
- Multi-Platform Complexity: Organizations often use a variety of platforms and systems for different purposes. Manually tracking orphan users across diverse platforms, such as cloud-based services, on-premises applications, and directories like Active Directory, demands a substantial investment of time and resources.
- Data Accuracy: Relying on manual processes increases the risk of inaccuracies in employee data. Ensuring that user profiles align with current employment status, roles, and permissions requires a consistent and error-free updating process.
- Timeliness: Prompt identification of orphan users is crucial for maintaining security. Manual processes may not be agile enough to detect changes in real-time, leaving organizations vulnerable to security breaches during the lag between an employee’s departure and the update of their user status.
- Audit and Compliance: Adhering to regulatory requirements and internal compliance standards demands meticulous record-keeping. Manually managing orphan users makes it challenging to maintain an auditable trail of user access changes, potentially resulting in compliance issues.
- Resource Drain: The manual identification and remediation of orphan users consume valuable resources. Human effort spent on repetitive and time-consuming tasks could be better utilized in strategic security initiatives.
- Lack of Centralization: In organizations where user data is decentralized across various systems, the lack of a centralized approach complicates the manual management of orphan users. Coordinating efforts across departments and platforms becomes a logistical challenge.
- Security Gaps: Human error in the manual identification process can lead to overlooking orphan users, creating security blind spots. These gaps may be exploited by malicious actors seeking unauthorized access.
- Scalability Challenges: As organizations grow, manual processes become increasingly untenable. Scalability becomes a concern, and the risk of overlooking orphan users rises proportionally with organizational expansion.
The importance of automated solutions, like Cypago, becomes evident, especially in the context of cross-functional collaboration between HR, IT, and Security teams, as current manual processes using email and spreadsheets may lack oversight and accountability, potentially leading to security black holes.
The Cypago Advantage: Automated Monitoring, Detection and Analysis of Orphan Users
UAR processes benefit immensely from automation – like Cypago’s Cyber GRC Automation (CGA) platform. Through advanced automation, Cypago seamlessly collects and analyzes user data across all of your environments, cross-referencing it with employee status.
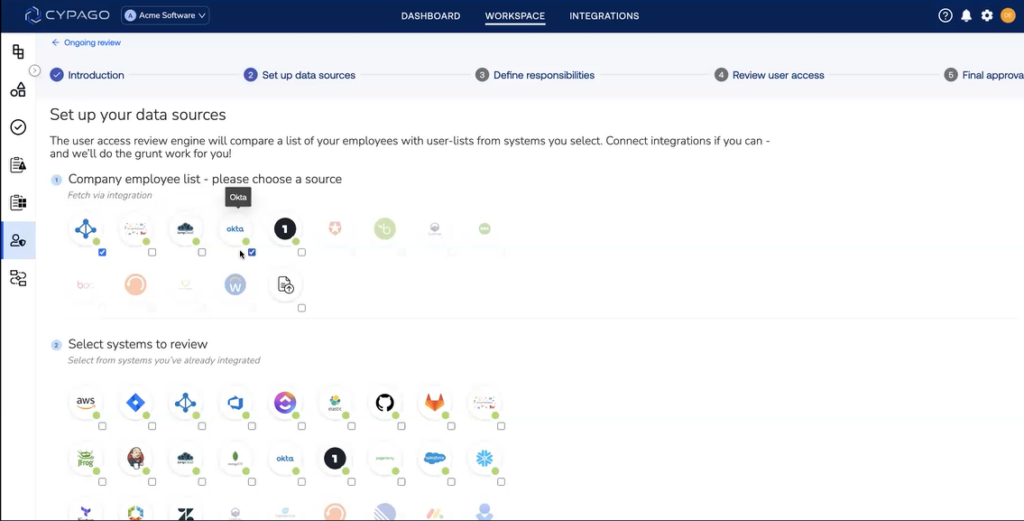
The primary goal is to identify orphan users – those individuals who do not have an active counterpart within the employee roster. This automated process not only streamlines the detection of security gaps but also significantly reduces the risk of human error inherent in manual management.
Detecting Orphan Users
Discovering orphan users with Cypago involves a systematic process during the User Access Review (UAR). Begin by aggregating user lists and employee data from diverse systems, ensuring a comprehensive overview. Cypago hones in on users with inactive, disabled, or terminated employee status, effectively pinpointing potential security loopholes.
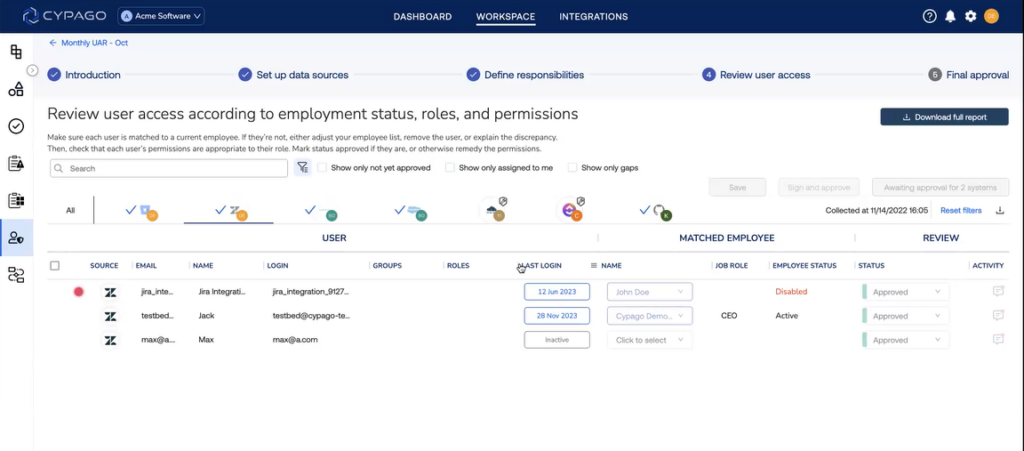
Detecting Dormant Users: A Comprehensive Approach
In addition to addressing orphan users, Cypago takes a holistic stance by monitoring dormant users within the User Access Review (UAR) process. The platform meticulously tracks various leave statuses, including standard leave and parental leave. By comparing this information with user activity indicators such as active or inactive status and last login, Cypago identifies any inconsistencies that might pose a security risk.
Proactive Security Alerts
Cypago’s notable feature lies in its ability to not only identify but also proactively respond to security gaps. Orphan users trigger automatic flags, accompanied by alerts and notifications sent to GRC, security and operations team. This immediate response mechanism is crucial for promptly addressing users misaligned with any active employees, mitigating security risks before they turn into threats.
Ongoing Security Through Continuous Monitoring
Detection is just the first step; sustaining ongoing security and compliance is equally essential. Cypago tackles this challenge through continuous monitoring and analysis of user scenarios. This approach ensures organizations stay ahead of potential threats, providing a robust solution for long-term security and compliance needs.
Tailoring to Specific Needs
Flexibility is a cornerstone of Cypago, allowing organizations to configure user access reviews according to their unique requirements and preferred review frequencies. Beyond orphan user detection, Cypago introduces features such as monitoring Segregation of Duties and the Principle of Least Privilege. Users gain the ability to define rules for detecting security or compliance gaps, offering a customized approach aligned with organizational policies.
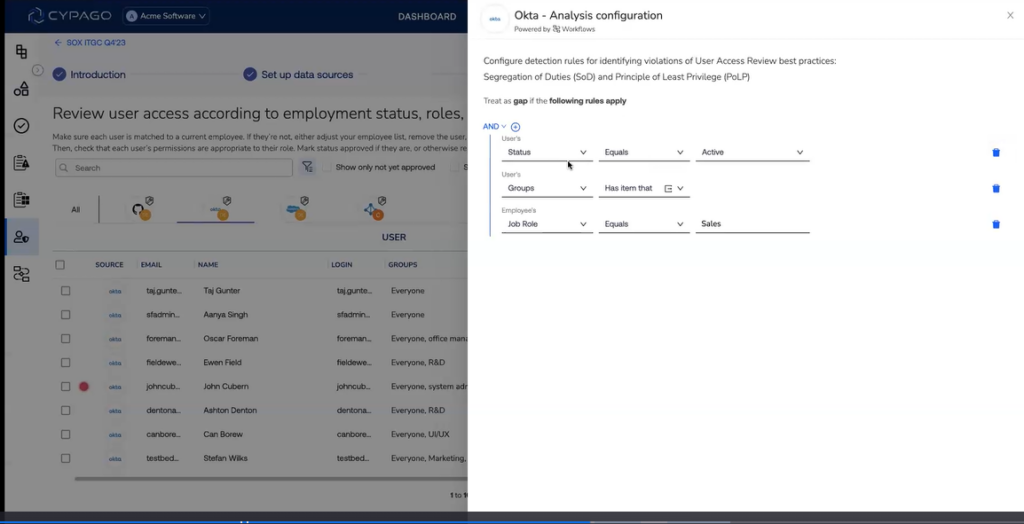
From Detection to Remediation: End-to-End Capability
Step into the world of effortless data security review and remediation with Cypago! Follow these simple steps to ensure a seamless process:
- Identify Areas Needing Attention: Mark specific areas that require attention and provide detailed reasons for clarity.
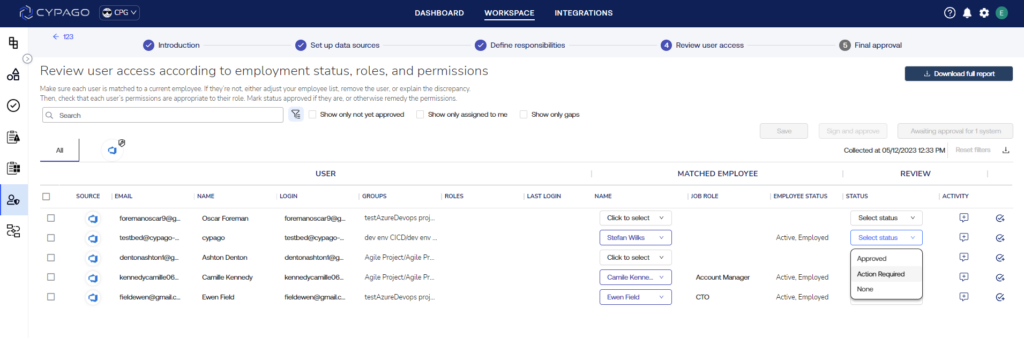
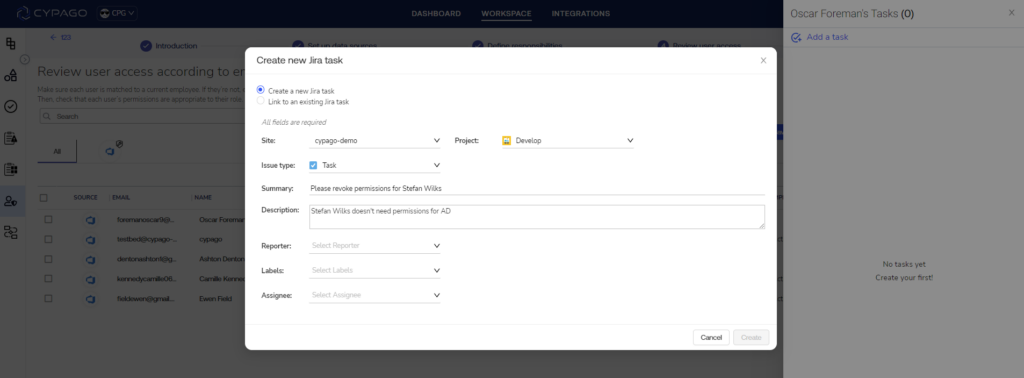
- Initiate IT Ticket and Assignment: Easily open an IT ticket and assign tasks directly to your IT personnel. Thanks to Cypago’s intelligent 2-way integrations with platforms like Jira, ServiceNow, Monday, and more, collaboration has never been smoother.
- Dynamic Permission Updates: Sit back and relax as Cypago dynamically updates permissions during subsequent scans, ensuring that your data remains secure and compliant.
- Comprehensive Activity Logging: Keep track of every change and activity throughout the review process. Cypago meticulously logs each step, providing a comprehensive audit trail for transparency and accountability.
- Approve permissions and download audit reports for internal and external uses.
Experience the efficiency and precision of Cypago – where securing your data is a step-by-step journey towards enhanced peace of mind.
Cypago – A Guardian Against Orphan User Threats
In a world where cybersecurity threats are ever-evolving, Cypago stands out as a formidable guardian against the menace of orphan users. By automating the detection process, providing real-time alerts, and offering customization options, Cypago empowers organizations to fortify their security infrastructure. As we navigate the complexities of user access management, Cypago emerges as a beacon, guiding organizations towards a safer and more secure digital future.
