In the ever-evolving landscape of Cyber Governance, Risk, and Compliance (GRC), staying ahead of potential risks is crucial for organizations. Today, we’re excited to announce some powerful enhancements to Cypago’s GRC integrated Risk Management features, bringing a new level of integration and customization to the fingertips of GRC managers.
Enhancing Interconnectivity: The Latest Updates to Our Risk Management Product
In our constant pursuit of providing a comprehensive and streamlined Risk Management solution, we are thrilled to announce a significant update to our platform that focuses on strengthening the interconnectedness between governance, risk, and compliance (GRC). This update not only enhances the user experience but also bolsters the effectiveness of risk mitigation strategies within your organization.
Linking Risks and Controls for Seamless Management
One of the key features of this update is the ability to link risks directly to their corresponding controls within the system. This functionality brings a new level of clarity and efficiency to risk management by establishing a direct relationship between identified risks and the controls designed to mitigate them. This linkage ensures that your organization can seamlessly navigate the complex web of risks and controls, allowing for more informed decision-making and precise risk mitigation strategies.
By facilitating the direct association between risks and controls, our Risk Management module empowers users to visualize the impact of controls on mitigating specific risks. This not only simplifies the risk management process but also enhances accountability and transparency throughout the organization.
Full Visibility into Risk Findings
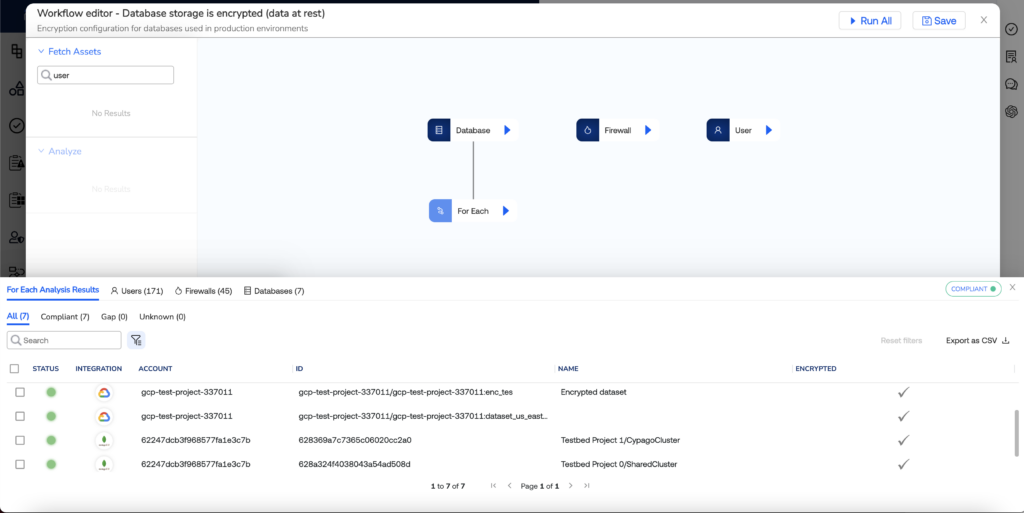
Another key feature is the ability to immediately gain full visibility into the findings. GRC managers can now navigate through a granular breakdown of findings associated with specific risks, enabling them to pinpoint areas of vulnerability and weakness. This newfound visibility empowers decision-makers to prioritize and strategize effectively, ensuring that resources are allocated where they are needed the most. Whether it’s identifying control weaknesses, compliance lapses, or process inefficiencies, Cypago’s Risk Findings feature delivers a level of transparency that is instrumental in fortifying an organization’s risk management posture.
Opening Tasks Directly from the Risk Management Panel
Another notable enhancement is the ability to open tasks directly from the Risk Management panel. This streamlines workflows and simplifies task management by allowing users to access and address assigned tasks without navigating through multiple screens. With this feature, users can efficiently tackle risk-related tasks, ensuring a swift response to potential threats and vulnerabilities.
This direct integration of tasks within the Risk Management panel promotes a more cohesive and responsive risk management approach. It minimizes the time and effort required to address identified risks, contributing to a more agile and proactive risk management culture within your organization.
Use Case: Understanding the Connection
Imagine a scenario where a GRC manager needs to address a specific risk identified in their organization. With Cypago’s new features, they can now directly link this risk to the corresponding controls in their frameworks. This not only enhances visibility but also facilitates a more strategic approach to risk mitigation.
Mitigation Treatment Plans
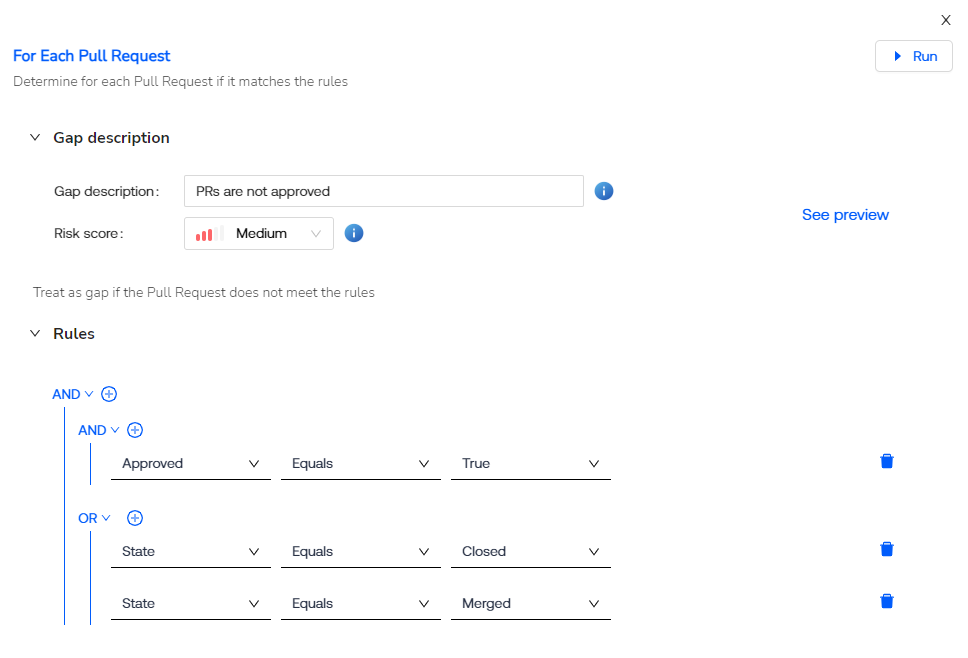
One of the standout features of this integration is the ability to select and customize a mitigation treatment plan for identified risks. GRC managers can now devise tailored strategies to address risks effectively, aligning them with specific controls within their organizational structure. These strategies are fully customizable and utilize all the information and evidence collected from their IT infrastructure to create the most effective course of action.
Findings and Gaps Analysis
Cypago takes it a step further by allowing users to view findings and identify potential gaps in their risk mitigation efforts. This nuanced approach empowers GRC managers to make informed decisions, ensuring that their risk management strategies are robust and effective.
Risk Matrix: A Foundation for Informed Decision-Making
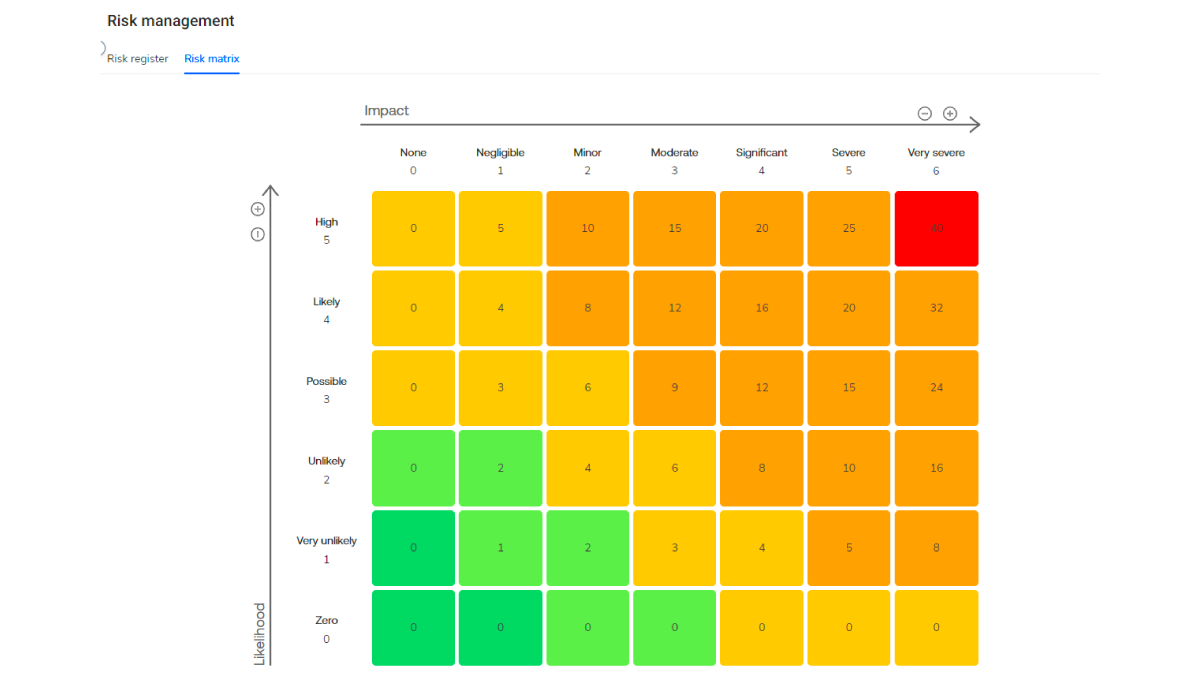
Cypago’s Risk Matrix, already deployed and operational, forms the bedrock of our risk management capabilities. It provides a visual representation of the likelihood and impact of identified risks, aiding organizations in making informed decisions on prioritizing and addressing potential threats.
What is a Risk Matrix?
A risk matrix is a visual representation of potential risks associated with a project, decision, or process. It is a tool used in risk management to assess and prioritize risks based on their likelihood and impact.
The matrix typically consists of a grid with two axes:
- Likelihood: This axis represents the probability or likelihood of a risk event occurring. It is often divided into categories such as low, medium, and high.
- Impact: This axis represents the potential consequences or impact of a risk event if it were to occur. Impact is also often categorized as low, medium, and high.
The intersection of the likelihood and impact categories creates a matrix where different risk levels can be identified. Each cell in the matrix corresponds to a specific combination of likelihood and impact, and it is assigned a risk level or priority. The risk levels may be color-coded or numbered to provide a quick visual indication of the severity of each risk.
The risk matrix helps organizations and project teams prioritize their efforts in managing risks. Risks falling in the high likelihood and high impact quadrant are usually given the highest priority and require more attention in terms of mitigation or contingency planning. On the other hand, risks in the low likelihood and low impact quadrant may be monitored but might not require significant resources for mitigation.
Cypago’s Risk Matrix: Tailor-Made for Enterprise
Our risk matrix feature provides users with a customizable approach to assess and prioritize potential gaps or risks within their projects or decision-making processes. This functionality allows users to selectively assign risk levels, such as high, medium, or low, to specific gaps based on their unique criteria. By empowering users to tailor the risk assessment according to their priorities, the feature enhances the flexibility and relevance of the risk management process. This customization capability ensures that organizations can efficiently allocate resources and attention to the areas that matter most, optimizing their risk mitigation strategies and contributing to more informed decision-making.
GRC Integrated Risk Management: Unifying Governance, Risk, and Compliance Efforts
The overarching goal of these updates is to reinforce the interconnectedness between governance, risk, and compliance, creating a holistic approach to organizational risk management. By seamlessly linking risks to controls and providing direct access to tasks, our Risk Management product offers a unified platform for managing the entire risk lifecycle.
This integration not only improves efficiency but also facilitates a more strategic and proactive risk management strategy. With a comprehensive view of risks and controls, organizations can make informed decisions, optimize resource allocation, and strengthen their overall risk posture.
In conclusion, these updates mark a significant step forward in our commitment to providing a cutting-edge Cyber GRC integrated Risk Management solution. We believe that the enhanced interconnectedness between governance, risk, and compliance will empower organizations to navigate the complex landscape of risks more effectively and proactively safeguard their assets and reputation.